[ad_1]
Within the quickly rising crypto trade, the widespread adoption of cryptocurrencies has attracted not solely reliable customers but in addition cybercriminals in search of to exploit vulnerabilities.
Latest findings from cybersecurity agency Kaspersky make clear a complicated malware assault focusing on Macbook customers within the crypto house.
Harvesting Delicate Information From Contaminated Mac Techniques
Kaspersky Lab consultants found that the attackers repacked pre-cracked functions as Bundle (PKG) information – a sort of file format generally used on Macbooks – and embedded a Trojan proxy and a post-installation script.
The malware-laden functions had been primarily distributed by way of pirated software program channels. As soon as customers tried to put in the cracked functions, they unknowingly triggered the an infection course of.
To deceive customers, the contaminated set up bundle displayed a window with set up directions, instructing them to repeat the appliance to the /Purposes/ listing and launch an software known as “Activator.”
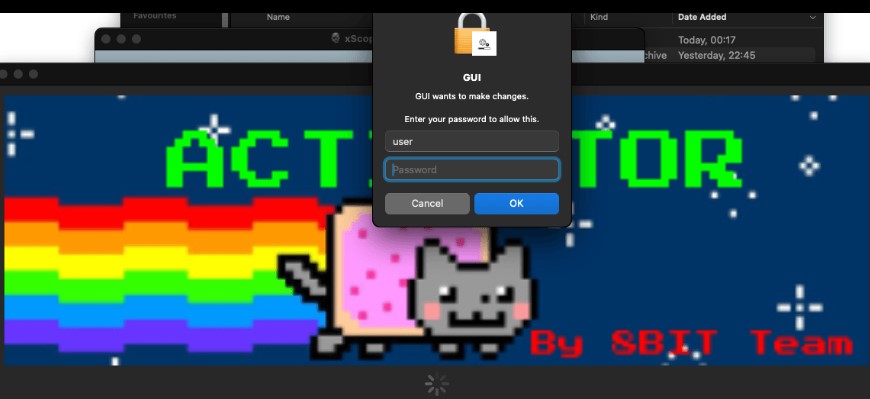
Though showing unsophisticated at first look, Activator prompted customers to enter a password, successfully granting the malware administrator privileges.
Upon execution, the malware checked the system for an put in copy of the programming language Python 3 and, if absent, put in a beforehand copied model of Python 3 from the Macbook working system listing.
The malware then ” patched” the downloaded app by evaluating the modified executable with a sequence hardcoded inside Activator. If a match was discovered, the malware eliminated the preliminary bytes, making the appliance seem cracked and useful to the consumer. Nonetheless, the true intentions of the attackers grew to become obvious because the malware initiated its essential payload.
The contaminated pattern established communication with a command-and-control (C2) server by producing a novel Uniform Useful resource Locator (URL), or net handle, by way of a mixture of hardcoded phrases and a random third-level area title.
This methodology allowed the malware to hide its actions inside regular DNS server visitors, making certain the payload obtain.
The decrypted script obtained from the C2 server – a distant server or infrastructure utilized by cybercriminals to regulate and handle their malware or botnet operations – revealed that the malware operated by executing arbitrary instructions obtained from the server. These instructions had been usually delivered as Base64-encoded Python scripts.
Moreover, the malware harvested delicate data from the contaminated system, together with the working system model, consumer directories, checklist of put in functions, CPU sort, and exterior IP handle. The gathered information was then despatched again to the server.
Malware Marketing campaign Targets Crypto Pockets Purposes
Whereas analyzing the malware marketing campaign, Kaspersky noticed that the C2 server didn’t return any instructions throughout their investigation and ultimately stopped responding.
Nonetheless, subsequent makes an attempt to obtain the third-stage Python script led to the invention of updates within the script’s metadata, indicating ongoing growth and adaptation by the malware operators.
Moreover, the malware contained features particularly focusing on well-liked crypto pockets functions, equivalent to Exodus and Bitcoin-Qt.
If these functions had been detected on the contaminated system, the malware tried to interchange them with contaminated variations obtained from a distinct host, apple-analyzer [.]com.
These contaminated crypto wallets included mechanisms to steal pockets unlock passwords and secret restoration phrases from unsuspecting customers.
The cybersecurity agency emphasised that malicious actors proceed to distribute cracked functions to realize entry to customers’ computer systems.
By exploiting consumer belief throughout software program set up, attackers can simply escalate their privileges by prompting customers to enter their passwords. Kaspersky additionally highlighted the methods employed by the malware marketing campaign, equivalent to storing the Python script inside a website TXT document on a DNS server, demonstrating the “ingenuity” of the attackers.
Featured picture from Shutterstock, chart from TradingView.com
[ad_2]
Source link



